Overview of Bad Rabbit Ransomware
As of October 24, a new ransomware “Bad Rabbit” is raging in Russia, Ukraine, Germany, and other countries. Unlike WannaCry, “Bad Rabbit” does not use EternalBlue, but launches watering hole attack to well-known websites and disguises as the Adobe Flash update program. When victims browse legitimate websites, forged Flash update pages will pop up to lure victims to download and install the media player, thereby infecting hosts.
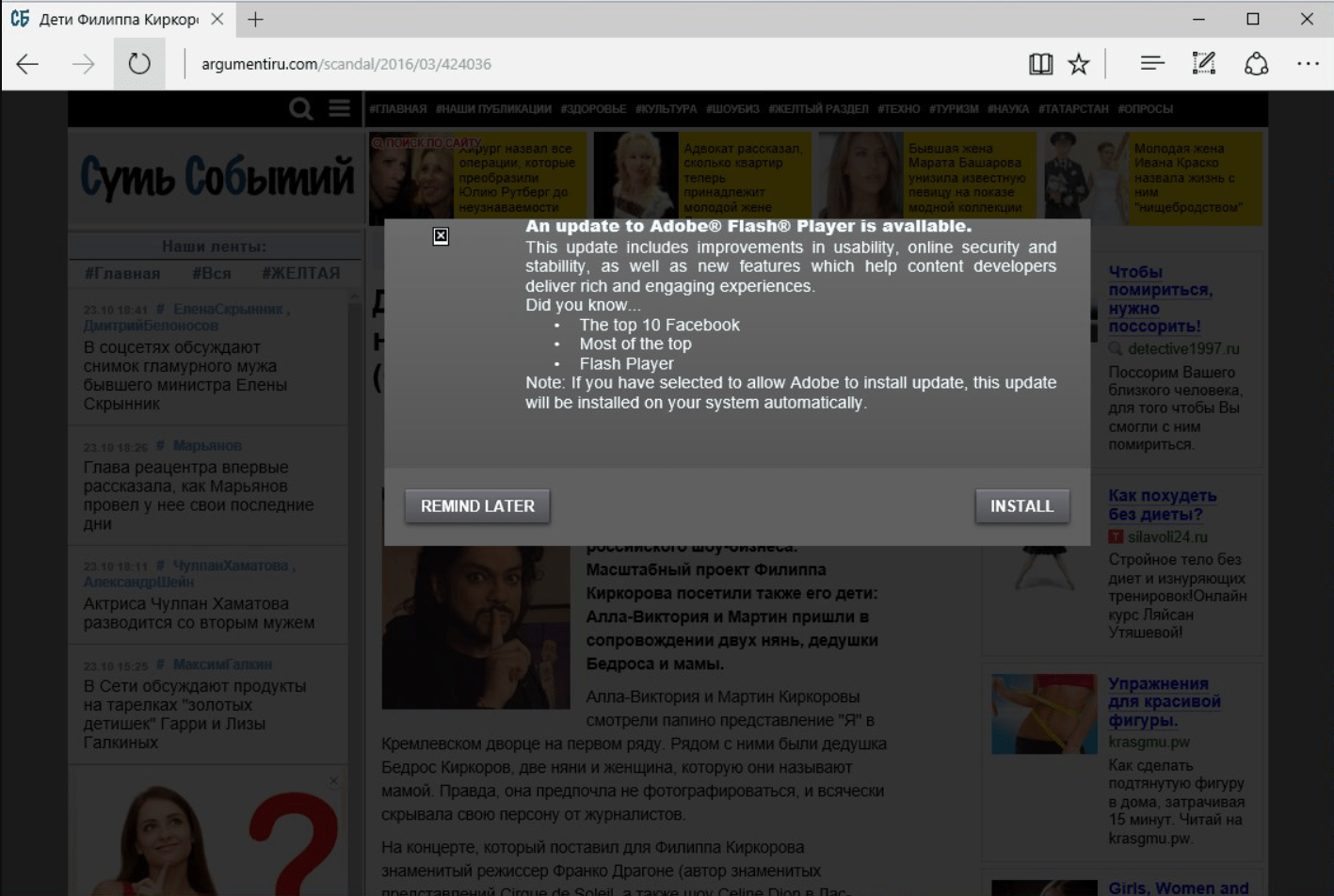
Figure 1: The false Adobe® Flash Player upgrade request on a Russian news website with Trojan virus when visited by a victim
Consequences
When the host is infected, the ransom note, illustrated below, appears to the victim to ransom 0.05 Bitcoin (about $282). In addition, “Bad Rabbit” will scan the ports that have enabled SMB protocols and attempt brute-force attacks through hard-coded, weak passwords and user name combinations to infect more systems. 23 websites, most of which are websites in Russian, have been hacked.
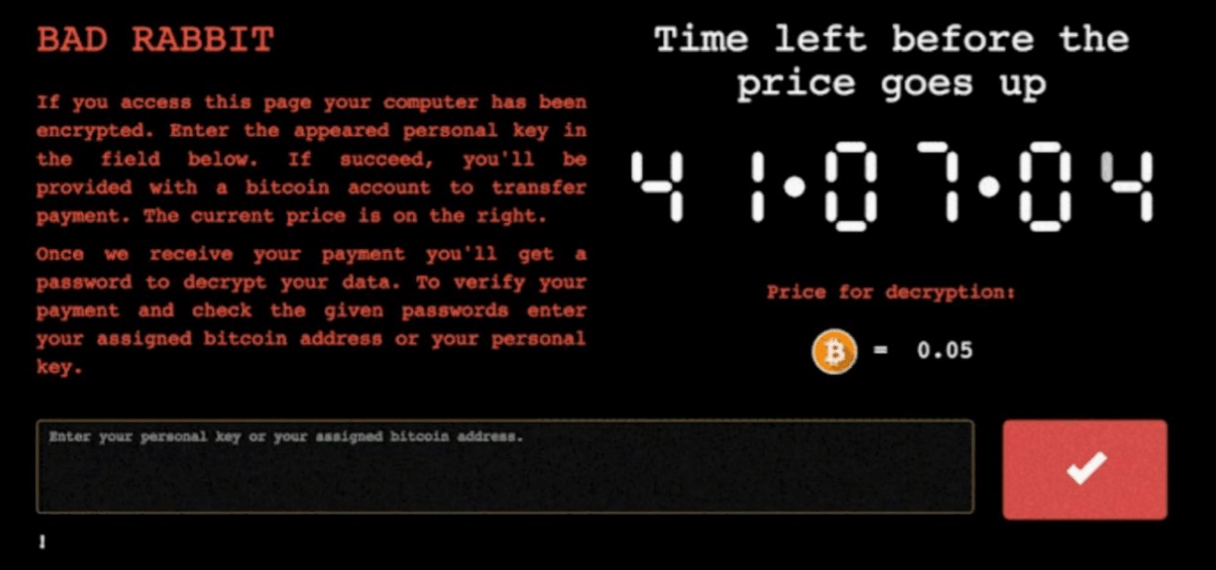
Figure 2: Ransom prompt during booting
Hillstone Response
Perimeter Protection:
Whether you’re running the Hillstone Next-Generation Firewalls (NGFW), intelligent Next-Generation Firewalls (iNGFW), IPS, CloudEdge or CloudHive deployed in a virtualized environment, the anti-virus and cloud sandbox functions can be enabled to block the ransomware download and provide network protection as part of the Hillstone layered security defense architecture.
- Anti-virus: the “Bad Rabbit” signature has been added in the Hillstone Networks virus filter signature library. Once the characteristics of the ransomware is matched, Hillstone security devices will block it directly.
- Cloud sandbox: once sandbox protection is enabled on Hillstone Networks security devices, it will be detected through the sandbox when unknown files are captured. If found as ransomware, it will send the threat intelligence to all devices that have enabled sandbox and block the ransomware download. A detection report will also be provided to let users understand the threat details more comprehensively.
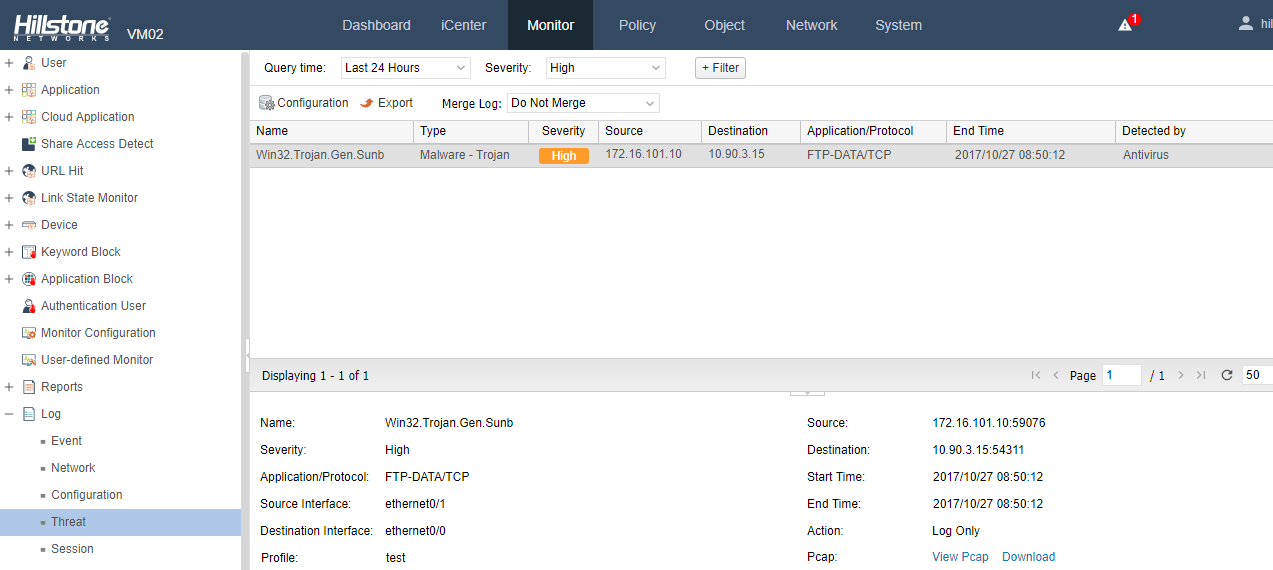
Figure 3: Anti-virus warning log
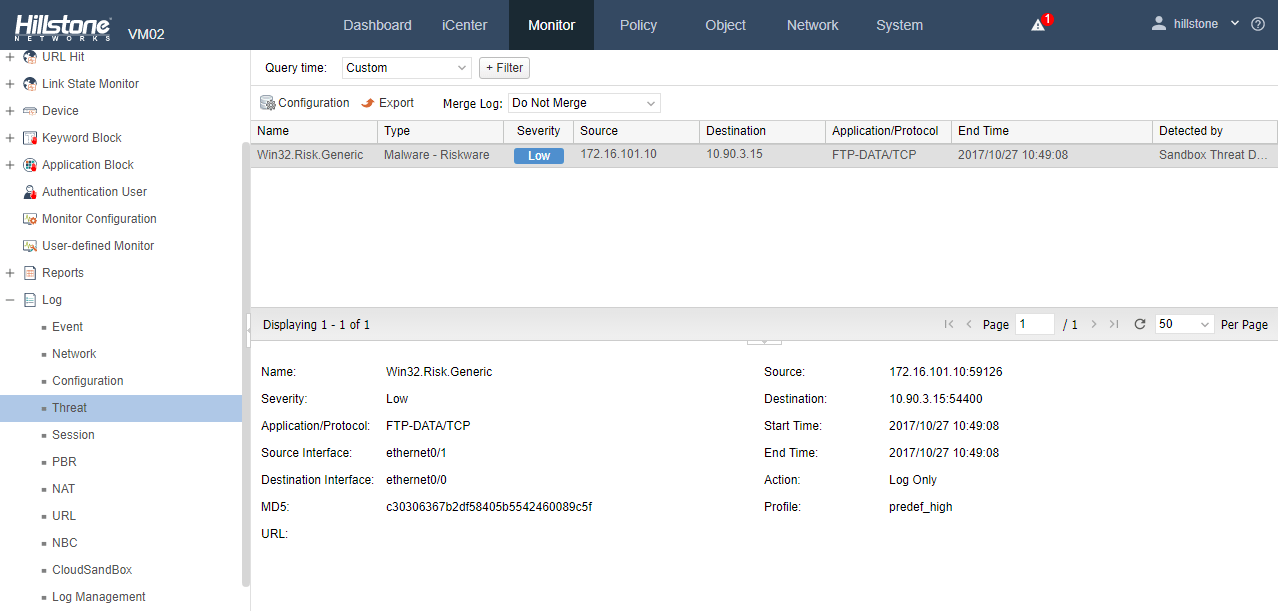
Figure 4: Cloud sandbox threat warning log
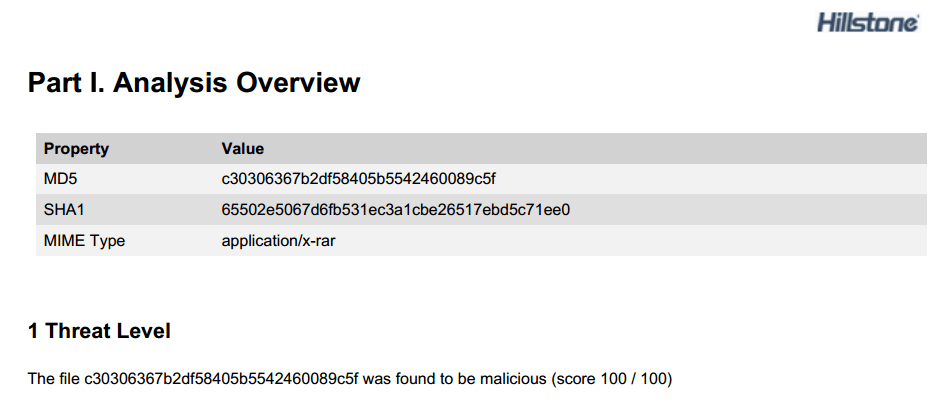
Figure 5: Cloud sandbox detection report
Intranet Protection:
“Bad Rabbit” may become history in the next few days, but ransomware is likely to evolve in the future and have new variants. To deal with new ransomware or variants, security vendors typically cannot add signatures in the library before the virus outbreak. However, Hillstone sBDS can detect the virus at the time of outbreak, as it uses intelligent security technologies such as machine learning and behavior analysis rather than the less effective virus signature characteristic match detection, to detect potential intranet threats and assess the intranet risk.
- Advanced threat detection: Hillstone sBDS can extract the malicious behaviors of the virus software and collect them into a model library. Once a variant or new virus breaks out, sBDS captures its malicious behavior and compares it with the model library. The closer the similarity, the higher the credibility of the event. It also represents a malware variant or virus in its family. This is illustrated in the following figures:
- Abnormal behavior analysis: Hillstone sBDS analyzes intranet hosts/servers through machine learning and mathematical modeling. The normal/abnormal behaviors of the host are recorded by periodic learning with the expected value set. Once the host behavior exceeds a threshold, the event will be presented in the threat view. See the following figures:
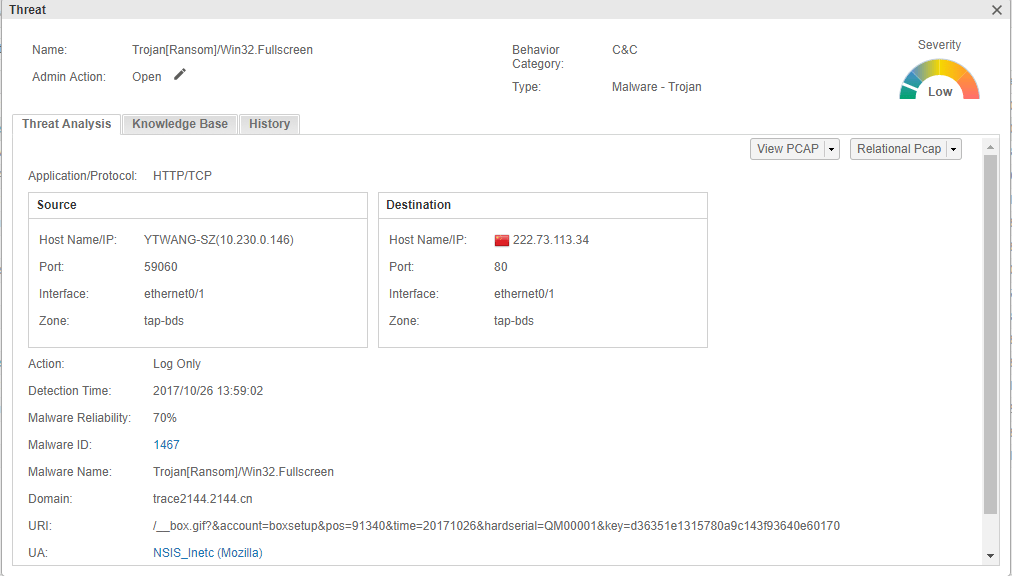
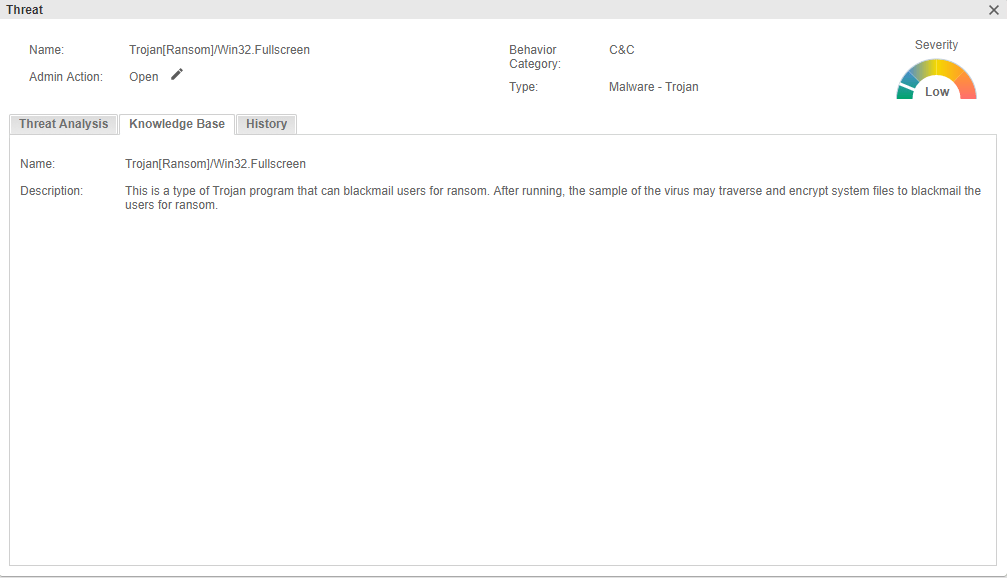
Figure 6: Advanced Threat Detection Example (not for this virus)
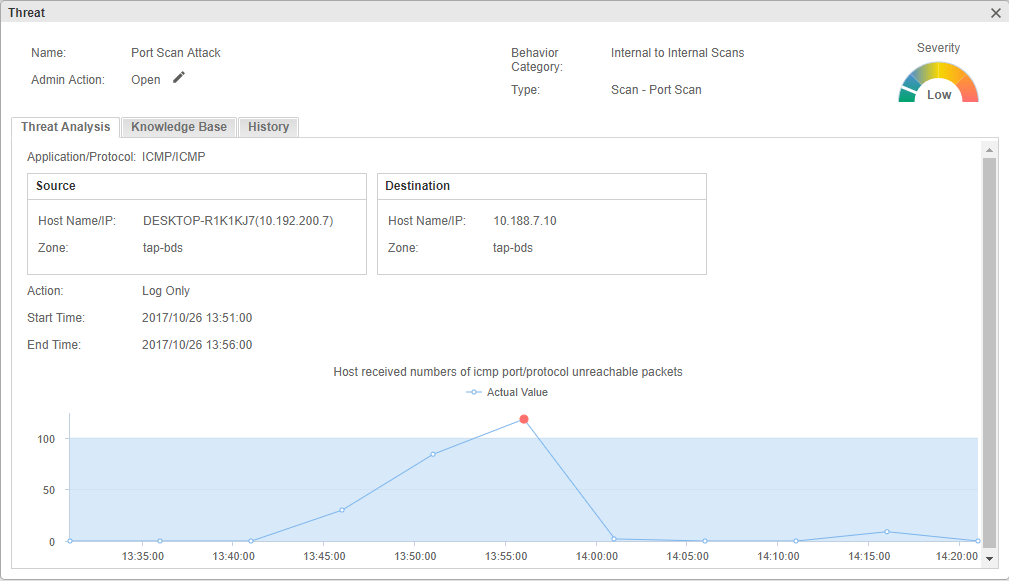
Figure 7: Abnormal behavior analysis example (not for this virus)
Defense and Fix Recommendations
Based on the current characteristics of the virus and the previous infection and prevalence of ransomware, Hillstone recommends:
- Do not download or run unknown files. Be wary of pop-up plug-in installation and upgrade prompts from the browser and webpages.
- Ensure your system is protected. Use the UAC control privilege or use the antivirus software from Microsoft Windows, or install a reliable antivirus software.
- Shut down 137,138,139,389,445,901 and other SMB service-related ports. If you need to enable SMB services, please use a strong password and change it often without saving the login credentials.
- Back up important documents on multiple devices, and keep the devices off-line or not fully accessible.
Hillstone is dedicated to securing the world’s networks. We are continually monitoring the Bad Rabbit ransomware and will keep our user community updated. For best practices on preventing ransomware, malware, unknown threats, please refer to Hillstone security service update.